When it comes to B2B prospecting, choosing the right partner can make all the difference in your sales and marketing efforts. Two leading names in the prospecting landscape are Bspec and Sopro. But which one offers the best value for your investment? In this SEO-friendly blog post, we’ll compare Bspec and Sopro across key categories to help you make an informed decision.
| Bspec | Sopro | |
|---|---|---|
| GDPR and CCPA | ✓ | ✖ |
| Multi source data prospecting | ✓ | ✖ |
| Deep company and decision maker verification | ✓ | ✖ |
| Multichannel approach | ✓ | ✓ |
| First-party intent data | ✓ | ✓ |
| Third-party intent data | ✓ | ✖ |
| Inbox Placement Technology | ✓ | ✖ |
| Average Cost Per Lead | $57.5 | $133 |
| Pay per successfully contacted Prospect | ✓ | ✓ |
| Pay per prospect attended Appointment | ✓ | ✖ |
GDPR and CCPA Compliance
First and foremost, compliance with data privacy laws like GDPR and CCPA is crucial. Both Bspec and Sopro meet these standards, ensuring your data is handled responsibly and legally.
Winner: Tie – Both Bspec and Sopro are GDPR and CCPA compliant.
Data Sources: Quality and Quantity
Bspec boasts a wide range of data sources, including Social Media, Official Registries, and High-End Enterprise Level data suppliers. This diverse data pool enables a more comprehensive prospecting process.
Sopro, on the other hand, focuses exclusively on Social Media for its data gathering, potentially limiting the depth of insights.
Winner: Bspec for its diverse and comprehensive data sources
Data Verification: Ensuring Accuracy
Data accuracy is paramount in prospecting. Bspec employs a multi-layered verification process, covering deep email verification, domain checks, website updates, and more.
Sopro primarily relies on email verification, which may not offer the same level of thoroughness as Bspec.
Winner: Bspec for its detailed and extensive data verification methods.
Multichannel Outreach: Reaching Your Audience
Bspec offers multichannel outreach through Email, Social Media, and Search Engines, allowing for a more integrated and effective marketing campaign.
Sopro limits its outreach to Email and Social Media, potentially missing out on broader audiences.
Winner: Bspec for its broader multichannel outreach capabilities.
Intent Data: Understanding Prospect Behavior
Understanding prospect intent is key to successful prospecting. Bspec provides both third-party and first-party intent data for deeper insights.
Sopro focuses solely on first-party intent data, offering a narrower view of prospect behaviour.
Winner: Bspec for its dual approach to intent data.
Inbox Placement Technology: Getting Your Message Seen
Email deliverability is crucial for campaign success.
Bspec uses in-house technology against 23 popular email service providers, achieving a 99% inbox placement rate.
Sopro relies on GlockApps for inbox placement, which may not offer the same level of reliability as Bspec’s in-house solution.
Winner: Bspec for its superior inbox placement technology.
Performance Metrics: Measuring Success
When it comes to performance, Bspec outshines Sopro with higher open rates, click rates, and lead conversion rates at a more affordable price.
| Performance Metrics | Bspec | Sopro |
|---|---|---|
| Open Rate | 70% | 60% |
| Click Rate | 20% | 15% |
| Lead Rate | 4% | 3% |
| Pricing Per Prospect | $2.3 | $4 |
| Cost Per Lead | $57.5 | $133 |
IWhen it comes to B2B prospecting, choosing the right partner can make all the difference in your sales and marketing efforts. Two leading names in the prospecting landscape are Bspec and Sopro. But which one offers the best value for your investment? In this SEO-friendly blog post, we’ll compare Bspec and Sopro across key categories to help you make an informed decision.
Understanding Harmful Emails
Harmful emails, often referred to as SPAM or JUNK emails, encroach upon our inboxes with various intentions, none of which bode well for the recipient. These electronic intruders can be categorized into three distinct groups, each posing its own set of threats.
1. Irrelevant Emails: Wasting Time and Resources
The first category encompasses the innocuous yet bothersome irrelevant emails. These digital detours divert our attention and consume our precious time without providing any discernible value. They might include promotions for unrelated products or services, newsletters that were subscribed to without much thought, or general announcements that bear no relevance to our personal or professional interests. These emails, although not directly malicious, drain productivity and foster a sense of digital clutter, underscoring the need for effective SPAM or JUNK guards.
2. Phishing Emails: Camouflaging for Deception
A more sinister facet of harmful emails is the realm of phishing. Phishing emails are cleverly designed to impersonate legitimate organizations or individuals, luring recipients into divulging sensitive personal information, such as passwords, credit card details, or even social security numbers. These fraudulent emails often create a sense of urgency, prompting recipients to take immediate action. It’s imperative to remain vigilant against these deceptive attempts to extract confidential information and undermine our digital security.
3. Malware-infested Emails: Concealing Threats
The third category comprises emails that harbor malicious intent beyond just soliciting information. These emails are embedded with malware, which, when opened or interacted with, can infiltrate our devices and wreak havoc. Malware can include viruses, ransomware, spyware, and other malicious software that jeopardize our privacy, security, and even the functionality of our devices.
Practical Strategies for Inbox Placement
To ensure that your legitimate emails avoid the spam folder, consider implementing the following strategies:
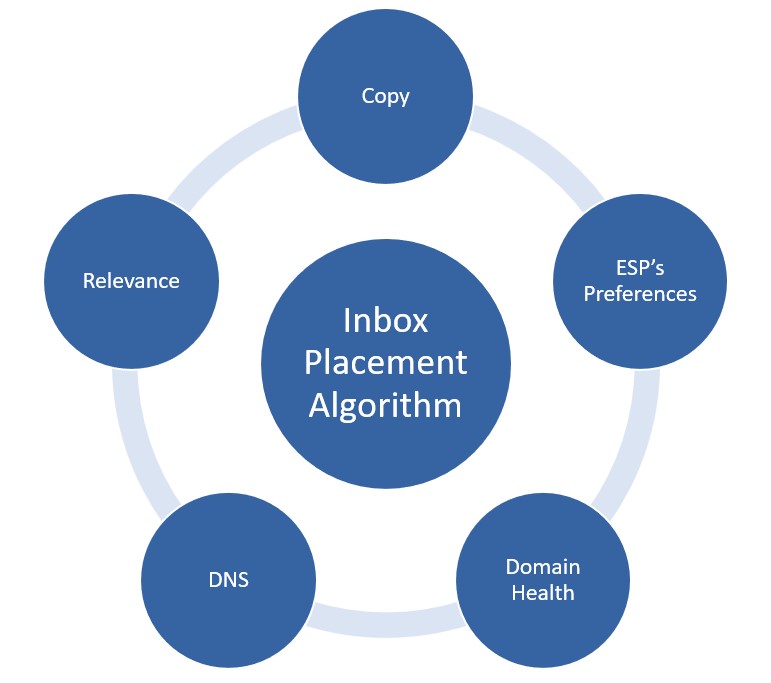
1. Polite and Well-Structured Copy:
Craft your email copy in a polite, non-aggressive, and well-structured manner. Include your name, phone number, and company address for authenticity. Keep the email body concise and avoid using excessive images, links, or colors that may trigger spam filters.
2. Targeted Proposition:
Tailor your email content to the specific recipient, ensuring that your proposition is relevant to their needs and interests. Personalized emails are less likely to be flagged as spam.
3. Email Service Provider (ESP) Preferences:
Familiarize yourself with the preferences of the recipient’s ESP. Some providers may have strict policies against images or links in initial communications. Adapt your email content accordingly to align with their guidelines.
4. Domain Health:
Ensure that your email domain has not been associated with mass mailing or other suspicious activities in the past. Using your primary domain is preferable, but if necessary, consider acquiring a new domain for analytical purposes.
5. DNS Setup:
Verify that your DNS settings, including MX records, SPF records, DKIM records, and DMARC records, are configured correctly. A well-maintained DNS setup can enhance the credibility of your emails.
In the realm of business-to-business (B2B) communication, the distinction between legitimate emails and spam or junk can sometimes be blurred. Despite well-intentioned efforts, emails that comply with local laws can still end up in the spam folder due to automated filters. To maximize your chances of inbox placement and ensure that your emails are read, it’s crucial to adhere to the five golden rules outlined above. By understanding the nuances of harmful emails and the role of SPAM or JUNK guards, you can navigate the digital landscape with confidence and security.




